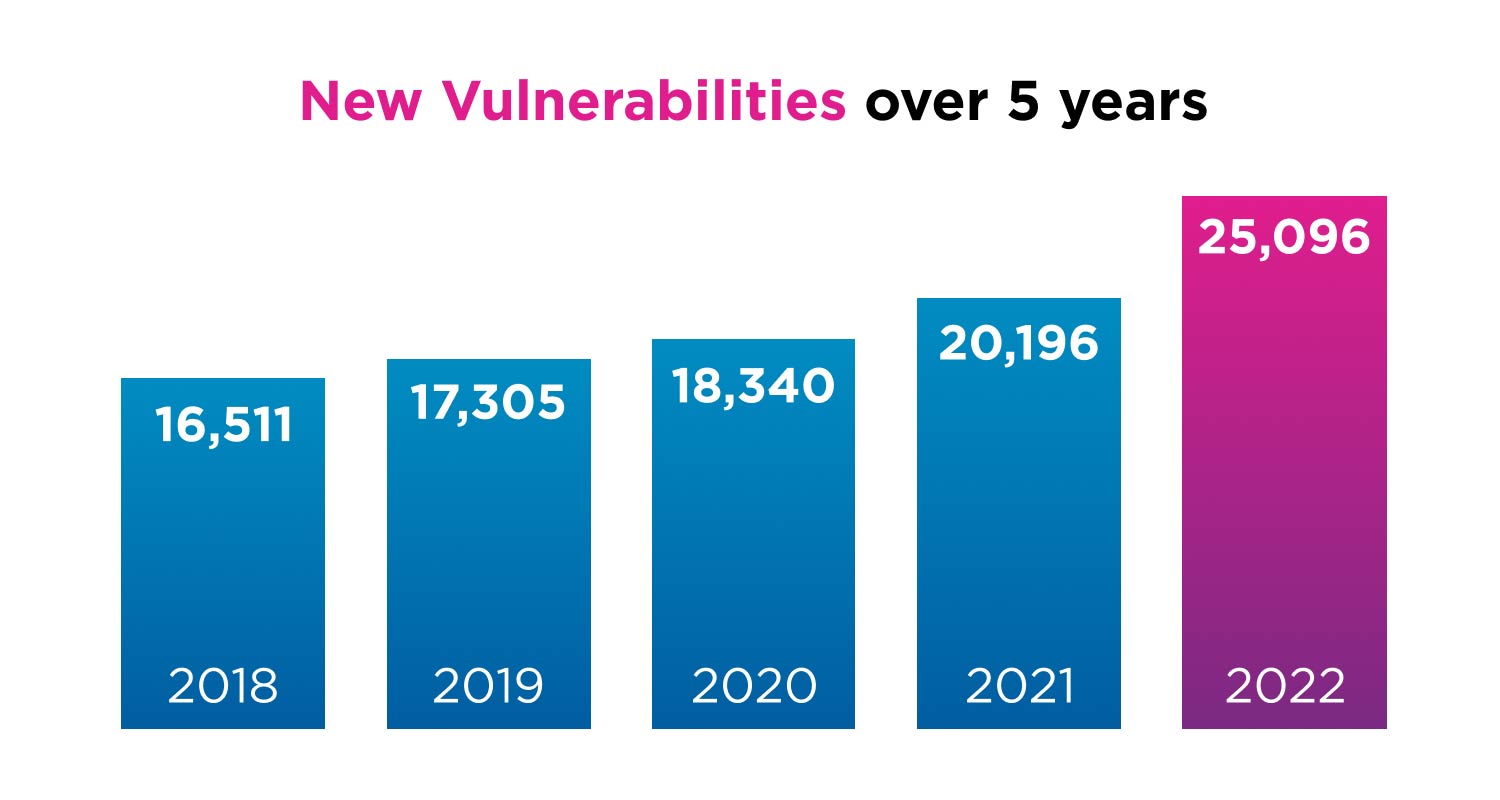
 In the realm of cyberrisk, the vulnerability landscape is vast. Skybox’s 2023 Vulnerability and Threat Trends Report noted over a staggering 25 000 new vulnerabilities and exposures recorded last year alone, marking a 25% year jump from the previous year. This increase happens while security teams often have to deal with reduced budgets and resources.
In the realm of cyberrisk, the vulnerability landscape is vast. Skybox’s 2023 Vulnerability and Threat Trends Report noted over a staggering 25 000 new vulnerabilities and exposures recorded last year alone, marking a 25% year jump from the previous year. This increase happens while security teams often have to deal with reduced budgets and resources.
Read: Vulnerability and Threat Trends Report 2023
While human attack vectors are a significant concern, it’s important to note that more than 40% of breaches are still occurring through software supply chain and 38% of attacks are via third-party access, while 46% are through web applications, as reported in the PwC 2023 Digital Trust Insights Report. Backdoor attacks and “living off the land” approaches are becoming more common, making it even harder for IT security to stay on top of threats.
So, what exactly is cyber exposure management? Think of it as applying sunscreen only to visible areas, like your arms or areas within easy reach. However, the real damage is only found when you realise that sunburn is usually to exposed skin that lies in less obvious places, like behind your knees or ears, where it’s been exposed to harsh UV rays while you focus on the visible areas. Full coverage is essential to prevent an uncomfortable night ahead!
Traditional approaches to handling vulnerabilities and patches are no longer enough due to the sheer volume and rapid evolution of vulnerabilities. Cybersecurity risks extend beyond software vulnerabilities, encompassing device misconfigurations, overlooked services, overly permissive filtering rules and more. The term “exposure” covers a broader spectrum of risks, urging security teams to reconsider traditional vulnerability management methods.
Just like the sunscreen analogy, addressing the challenge of organisational cyberrisks based solely on what a tool reports or what can be seen from one dimension lacks valuable insights and won’t prevent the unseen patch of skin from being scorched – such as that forgotten unmanaged development server that is internet-facing and stores critical financial data.
Organisations will continue to face gaps in effectively managing risks and threats when they have not implemented a continuous exposure-based approach, primarily because their existing security controls are siloed and tool-centric. These tools can only do so much. For example, firewalls may successfully filter traffic, but what about firewalls with overly permissive rules?
Additionally, many organisations have rigid compliance programmes in which they audit areas like firewalls and network segmentation and carry out penetration testing at intervals. But even these measures sample only selected areas of the network and indicate the level of risk at a single point in time. This would be akin to applying sunscreen once and going for a swim straight after and never reapplying the cover.
Scheduled audits and pentests often neglect areas considered irrelevant, such as the laptop that hasn’t been patched for the year, or the server that’s just a sandbox, but is in fact exposed to the internet from where attackers could access the network. The attack surface evolves continuously, necessitating ongoing exposure management. Organisations must maintain an up-to-date, real-time view of their environment – with all the data normalised to help them gain insights and act on prioritised risks and be able to rapidly respond to vulnerabilities that pose an imminent and high risk.
Skybox CEM
Given the catastrophic impact of cyberattacks, organisations must adopt a comprehensive and proactive approach to risk mitigation. They need to continuously adapt as their exposure changes. Recognising this need, Skybox introduced a method to extend the scope of typical vulnerability management through a continuous exposure management (CEM) programme.
Through CEM, Skybox supports every aspect of an organisation’s continuous exposure management programme, enabling security teams to map their attack surface, contextualise data, evaluate and prioritise vulnerabilities, and respond effectively through remediation.
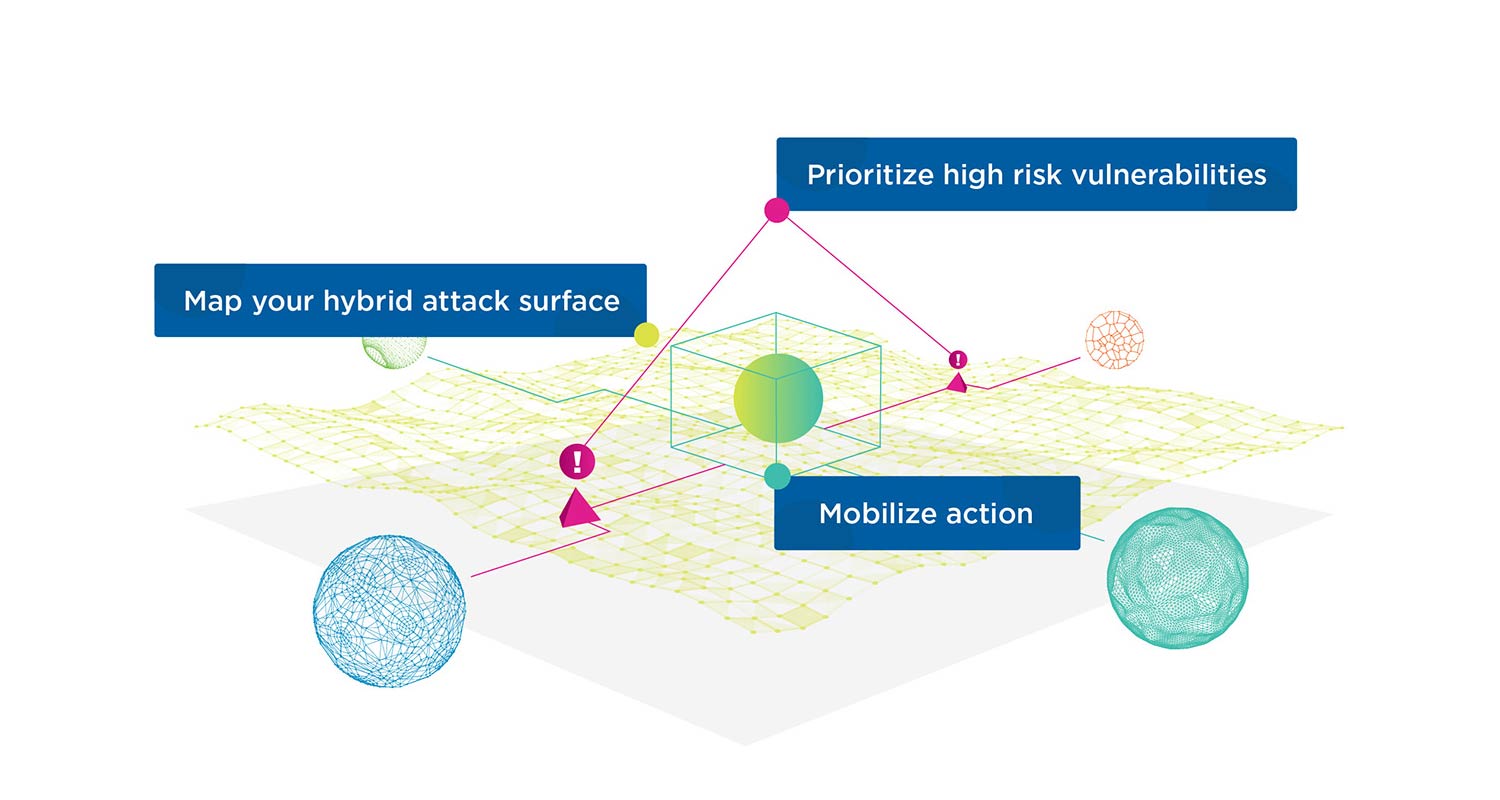
Skybox integrates with over 150 technologies to create a dynamic security model, mapping the attack surface and contextualising security data from various sources like network platforms, asset databases, security tools, vulnerability scanners, intelligence feeds and remediation systems. This aggregation of data offers a 360-degree view of the attack surface, delivering a thorough understanding of asset information, vulnerability and threat data, security controls and policies.
Through vulnerability prioritisation, we assess the exposure, exploitability and context of the asset to determine the severity of the risk. Not all risks represent the same danger for an organisation, therefore prioritisation looks at where the assets and data are in the network, how critical they are for the business, and what security controls are in place to protect them.
With Skybox CEM, organisations gain the full visibility necessary to understand the consequences of making changes or modifications to their infrastructure such as integrating a new branch, merging with another company, installing new applications, or migrating to the cloud. Armed with this understanding, they can ensure that security policies remain compliant and that teams are effectively reducing exposure to risks.
Attack simulations
This visibility also enables teams to run attack simulations to understand how they are exposed, the potential impact of this, and how they could contain the incident as attackers move laterally through the network.
Importantly, the Skybox CEM platform enables organisations to quantify both technical risk and the risk to business processes and revenues. It becomes possible to determine the costs per time frame if the business loses a particular system or application.
By prioritising and quantifying the risks, CEM enables IT security teams to address the most critical vulnerabilities first and prevent attacks before they happen – where it matters most.
- The authors are Simone Santana, Africa regional director, and Jose Bernal, Emea sales engineering director, both at Skybox Security
- Read more articles by Skybox Security on TechCentral
- This promoted content was paid for by the party concerned




