 Skybox Security’s recently published Mid-Year Vulnerability and Threat Trends Report 2021 found increased activity of cybercrime.
Skybox Security’s recently published Mid-Year Vulnerability and Threat Trends Report 2021 found increased activity of cybercrime.
Among the usual threat suspects, there is also a boom in cryptomining malware and ongoing growth of ransomware. There are now even malware-as-a-service and off-the-shelf tools that make attacks ready-packaged for bad actors.
Being a smooth cybercriminal has never been easier. You don’t have to be a clever hacker to be a security danger — you just need a nefarious plot and gall to exploit a company or government’s vulnerabilities.
Our research analysts discovered that companies are increasingly vulnerable in sensitive areas such as operational technology (OT) and network devices, which put vital infrastructure at risk. Compounding security complexity is an international ecosystem and digital marketplace that allows attackers to move money and collect ransoms easy, making cybercrime a big business that’s hard to prosecute.
Despite the doom and gloom of a digital world being more dangerous and hybrid cloud networks more complicated to secure, the report concludes on a positive note: the emergence of a modern security posture-management platform that performs real-world hybrid network exposure analysis as a powerful combatant against attacks. Security posture management provides comprehensive visibility across the entire network, allowing companies to precisely identify the most salient threats and facilitate timely, cost-effective remediations.
For chief information security officers, the evolution of exposure analysis — coupled with network policy and vulnerability management — is good news to an otherwise scary story.
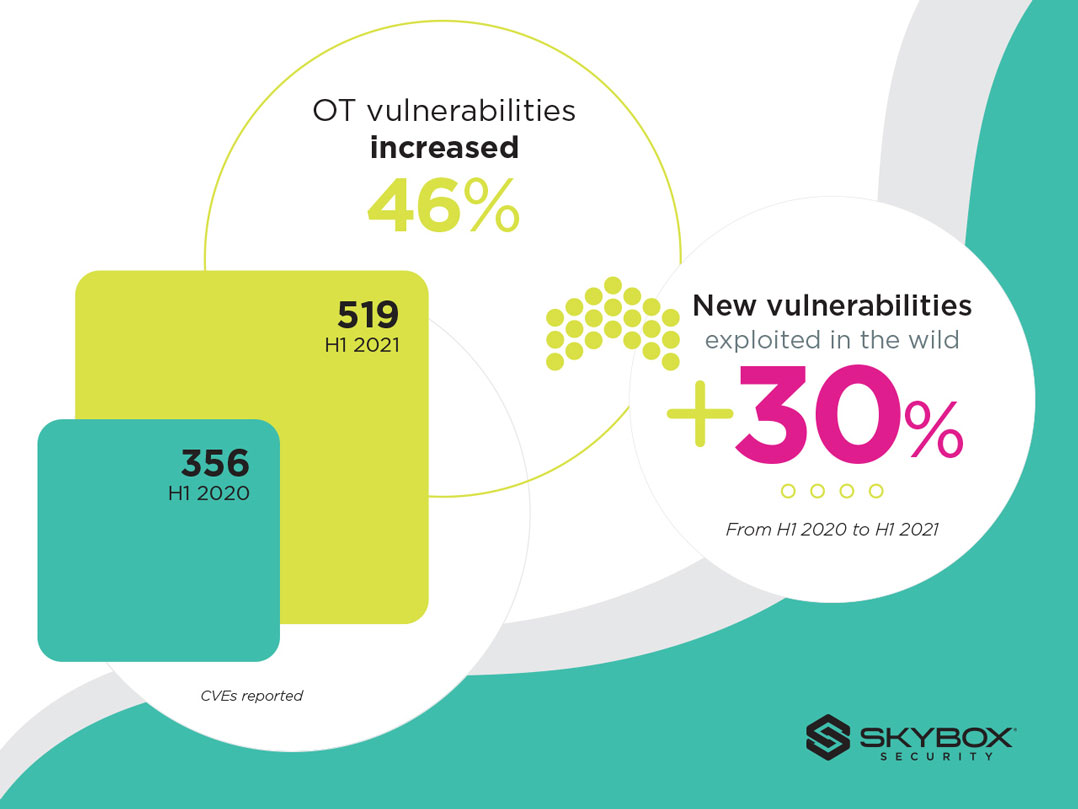 Here is a cross-section of key findings presented in the Skybox report:
Here is a cross-section of key findings presented in the Skybox report:
- Overall vulnerabilities continue to climb: There were 9 444 new vulnerabilities reported in the first half of 2021, not far behind last year’s record-setting pace. These new vulnerabilities add to a huge cumulative total, making it harder than ever for security organisations to target remediation efforts on the most urgent threats.
- OT vulnerabilities surge, putting critical infrastructure at risk: New vulnerabilities in OT were up nearly 50% versus the first half of 2020. These vulnerabilities pose a growing threat to critical infrastructure and other vital systems, a fact made manifest in a series of high-profile attacks on facilities such as oil pipelines, water supplies and food processing facilities. To make matters worse, it can be difficult or impossible to eliminate OT vulnerabilities through scanning and patching.
- Threat actors are taking increasing advantage of vulnerabilities: More vulnerabilities mean more opportunities for exploits, and threat actors are taking advantage. The number of vulnerabilities exploited in the wild increased 30% relative to the same period last year.
- Cryptojacking is the hot new malware trend: While new malware samples increased in almost every category, cryptojacking topped the list. Instances of this type of malware, which hijacks computer systems for cryptocurrency mining, more than doubled. This is just the latest example of how dynamic an industry malware has become, quickly adapting its offerings and business models to serve emerging markets.
- Network infrastructure is increasingly at risk: Network device vulnerabilities rose by nearly 20% compared to the first half of 2020. Products such as routers, VPNs and firewalls — intended to power and protect networks — are in many cases providing new entry points for malicious actors. As with OT systems, network devices can be difficult to scan and patch.
To learn more proprietary insights about the state of security and cybercrime, download the report.
About Skybox Security
Over 500 of the largest and most security-conscious enterprises in the world rely on Skybox for the insights and assurance required to stay ahead of dynamically changing attack surfaces. Our Security Posture Management Platform delivers complete visibility, analytics and automation to quickly map, prioritise and remediate vulnerabilities across your organisation. The vendor-agnostic solution intelligently optimises security policies, actions and change processes across all corporate networks and cloud environments. With Skybox, security teams can now focus on the most strategic business initiatives while ensuring enterprises remain protected. We are Skybox. Visit www.skyboxsecurity.com for more information or check out all the recent Skybox Security content on hub.techcentral.co.za/skybox.
- This article was written by Ran Abramson, security analyst at Skybox Research Lab
- This promoted content was paid for by the party concerned

