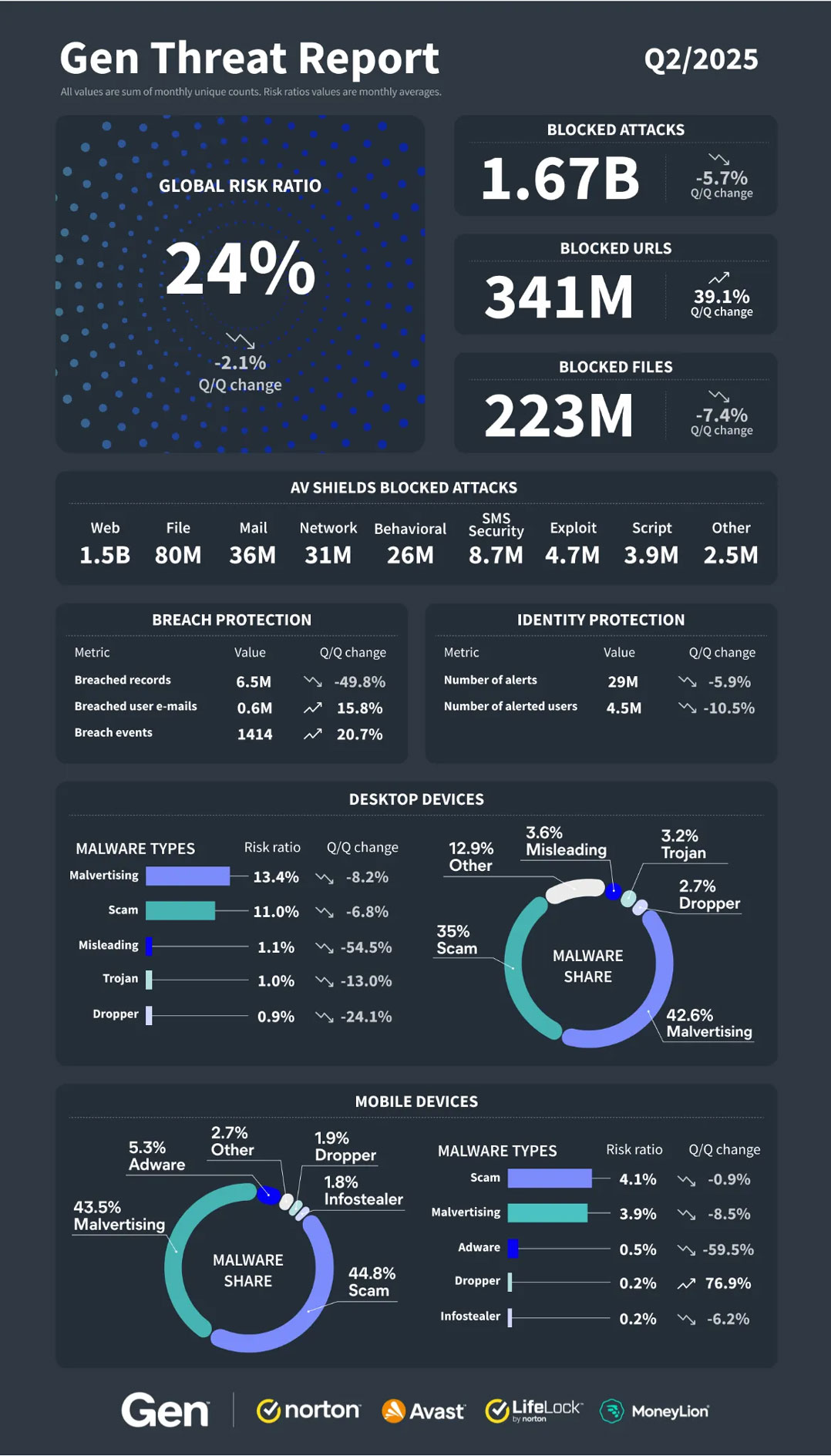
 As AI accelerates both innovation and risk, Gen Digital’s Q2 2025 Threat Report delivers a clear message: cybercriminals are using technology smarter – and more personally – than ever before. Their findings span AI-powered ransomware, pharmaceutical fraud, social media scams, and a surge in remote access attacks. Let’s unpack the most urgent threats facing consumers and organisations today.
As AI accelerates both innovation and risk, Gen Digital’s Q2 2025 Threat Report delivers a clear message: cybercriminals are using technology smarter – and more personally – than ever before. Their findings span AI-powered ransomware, pharmaceutical fraud, social media scams, and a surge in remote access attacks. Let’s unpack the most urgent threats facing consumers and organisations today.
1. Pharma fraud – fakes masquerading as medicine
Gen uncovered more than 5 000 fake pharmacy domains promoting high-demand medications – from antibiotics to weight-loss drugs and sexual health treatments. These pharma-fraud scams are sophisticated operations using polished websites, AI-generated review content, malicious code injection and search manipulation to appear legitimate.
In the second quarter of 2025, Gen blocked a million attacks tied to these domains – exposing a global fraud scheme built to harvest financial and personal data under the guise of discounted prescriptions.
2. AI-powered ransomware – the FunkSec case
The report details the takedown of FunkSec, the first ransomware strain partially developed with generative AI. Despite its ability to encrypt data and extort users, Gen researchers uncovered a cryptographic weakness – one that allowed victims to recover their files without paying ransom. A free decryptor was released via Avast, and FunkSec has since gone silent.
This case marks a milestone: even AI-enhanced malware can carry exploitable flaws, if diligently analysed.
3. Surge in financial and sextortion scams
From April to June 2025, financial scams surged 340%, many traced to fake ads and pages on Facebook using deepfake videos and chatbot forms to coax people into revealing sensitive information under the pretext of legal or investment help.
Meanwhile, sextortion scams doubled, rivalling phishing in their growth and psychological impact. These scams increasingly targeted mobile users, using urgency and manipulatory scripts to extract compliance.
4. Technical support scams via Facebook
Technical support scams rose nearly 65% globally, with 14% of blocked threats linked to Facebook. Fake Messenger-style popups locked browsers, displaying urgent messages prompting users to call fake support lines. The reach and credibility of Facebook’s ad network made it fertile ground for fraud.
5. The broader threat landscape
Other ley metrics from the report include:
- A 21% increase in data breach events, with breached e-mail counts up 16%;
- A 317% spike in malicious push notifications disguised as system alerts;
- A 62% rise in remote access attacks, led by Wincir RAT and misuse of cloud services like OneDrive; and
- Persistence of the Lumma Stealer, which resurfaced after takedown attempts using new infrastructure for data exfiltration.
Collectively, these figures reflect an increasingly automated, AI‑powered and socially engineered cybercrime ecosystem.
…article continues below…
 Why the Q2 report matters
Why the Q2 report matters
- Personalisation enables persuasion: Threat actors now tailor scams using AI-generated content (health blogs, influencer endorsements, fabricated reviews), creating a veneer of credibility that lures victims into trusting and engaging.
- AI accelerates scale – but leaves flaws: The FunkSec example demonstrates that AI can speed up malware development – but also generate errors that defenders can exploit. Continuous research and collaboration remain essential.
- Social platforms amplify threat spread: Platforms like Facebook and YouTube are weaponised to launch fraud at scale. Fake profiles, malvertising, deepfakes and AI personas blur the lines – and amplify reach.
 How to stay protected
How to stay protected
- Question “too good to be true” offers online: Low-cost prescription drugs via unfamiliar pharmacies are often scams. Look for secure checkout, reputable contact info and legitimate payment methods.
- Trust security tools: Decrypt your files yourself if caught by ransomware – tools like Avast’s FunkSec decryptor prove it’s possible.
- Limit data exposure on social platforms: Don’t click ads promoting “legal services” or investment schemes on Facebook; turn off browser pop-ups and close suspicious windows.
- Stay cautious with unsolicited tech support: Legitimate help won’t lock your browser or demand payment via phone.
- Enable mobile protections: Push notifications are a common malware vector. Ensure your OS and security apps are up to date.
- Use comprehensive security suites: Gen’s Norton and Avast brands, via tools like Norton Genie, offer AI‑powered scam detection and device protection.
 Final thoughts: the AI/cybersecurity paradox
Final thoughts: the AI/cybersecurity paradox
Gen Digital’s Q2 2025 Threat Report underscores a worrying reality: cyberthreats are evolving faster and are getting smarter and more dangerous, fuelled by AI tools that empower criminals to personalise, scale and evade detection.
Yet the same technologies also empower defenders. From decrypting AI-built ransomware to blocking scams before they reach users, proactive defence strategies are working – and proving effective.
Avast and AVG’s role in protecting against evolving threats
As cyberthreats continue to grow in complexity, Avast and AVG stand at the forefront of providing reliable, cutting-edge protection for businesses and individuals. With AI-powered threat detection, real-time security monitoring and robust defences against ransomware, scams and APTs, both Avast and AVG ensure that your digital environment remains secure.
For IT service providers and managed service providers, Avast and AVG offer tailored solutions through the Avast Business Hub, an all-in-one platform that simplifies security management. This platform is designed to protect users and devices from emerging threats, while reducing overhead and enhancing operational efficiency.
By combining advanced AI technology, machine learning capabilities and a team of global cybersecurity experts, Avast and AVG help you stay one step ahead of attackers, safeguarding your business against the evolving threat landscape.
 About Avert IT Distribution
About Avert IT Distribution
Partnering with Avert IT Distribution means investing in your success and growth. As a world-class distributor, we offer a superior range of cybersecurity solutions to protect your clients and your reputation. Founded in 2004, AvertITD has continued to expand and evolve. We are proud to serve partners across Africa, prioritising accountability, integrity and commitment in all that we do. These principles are embedded in everything you, as a reseller, offer to your customers.
To become an AvertITD reseller, complete this form or contact sales on +27(0)10-007-4430 (Johannesburg) or +27(0)21-007-2655 (Cape Town), or e-mail [email protected]. Find AvertITD on LinkedIn. Or send us a message on WhatsApp.
Contact AvertITD via WhatsApp
Our new WhatsApp support channel enables instant communication for partners and customers. Whether you need quick assistance, have questions about Avast or AVG licences, or want to discuss business requirements, you can now reach out directly for immediate help. This service ensures rapid responses across Africa, eliminating the need for lengthy e-mails or waiting for callback appointments.
Real-time support through live chat
In addition to WhatsApp, AvertITD has introduced a live chat feature on its updated website. This allows you to connect instantly with knowledgeable representatives who can answer your questions, assist with Avast and AVG solutions, and offer personalised guidance. The chat feature ensures you receive fast and efficient support without having to navigate through complex menus. By combining WhatsApp and live chat, AvertITD guarantees that partners and customers can easily access expert support, whenever they need it.
About Gen
Gen is a global company dedicated to powering digital freedom with a family of trusted brands including Norton, Avast, LifeLock, Avira, AVG, ReputationDefender and CCleaner. Our trust-based solutions help protect nearly 500 million users in more than 150 countries.
- Read more articles by Avert IT Distribution on TechCentral
- This promoted content was paid for by the party concerned




