 Recent cyber breaches and attacks have proven that cybersecurity is a real and present danger to most companies. IT’s role in business and organisations has changed significantly in the past 10 years. Companies rely on IT to be able to conduct business, render services and to manufacture products. Even traditional non-IT-reliant companies (mining, manufacturing) are increasingly connecting operational technology to their IT networks and thereby exposing Scada (supervisory control and data acquisition) and other manufacturing systems to the risks associated with cyber threats. The 2018 Allianz Risk Barometer shows that the biggest risk currently facing companies is cybersecurity/cybercrime and related business interruptions. In another study, conducted by Ernest & Young in 2018, perfectly illustrates the increased risk faced by mining companies from cyber threats.
Recent cyber breaches and attacks have proven that cybersecurity is a real and present danger to most companies. IT’s role in business and organisations has changed significantly in the past 10 years. Companies rely on IT to be able to conduct business, render services and to manufacture products. Even traditional non-IT-reliant companies (mining, manufacturing) are increasingly connecting operational technology to their IT networks and thereby exposing Scada (supervisory control and data acquisition) and other manufacturing systems to the risks associated with cyber threats. The 2018 Allianz Risk Barometer shows that the biggest risk currently facing companies is cybersecurity/cybercrime and related business interruptions. In another study, conducted by Ernest & Young in 2018, perfectly illustrates the increased risk faced by mining companies from cyber threats.
So how do companies, which sometimes don’t even have a full-time CIO, go about tackling the cybersecurity challenge? They usually rely on IT vendors and outsource partners to supply off-the-shelf software and hardware solutions (firewalls and endpoint security solutions), which might not adequately address the risk and still leave the company vulnerable.
The King IV code, principle 12, places the responsibility for information security lies with the board or governing body and this includes mitigation of technology and information risks faced by the organisation. An organisational information security review would give the board of directors adequate information about the information risks the company faces, the impact should these risks not be addressed as well providing a road map for implementing a cybersecurity programme and capability.
So why choose a cyber/Information security review over a security audit or a penetration test?
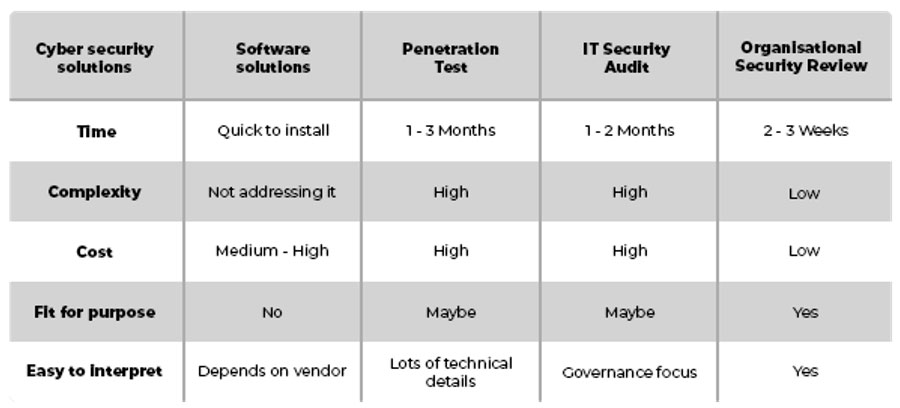 None of the options to address information/cyber risks — other than a organisational security review — is fit for purpose. Buying software seems like the easiest solution, but software alone won’t ensure cybersecurity, and will most likely take time to customise, will need a time period to test and must should be correctly installed and updated.
None of the options to address information/cyber risks — other than a organisational security review — is fit for purpose. Buying software seems like the easiest solution, but software alone won’t ensure cybersecurity, and will most likely take time to customise, will need a time period to test and must should be correctly installed and updated.
A penetration test (or “pentest”) is a very technical and expensive exercise, where a security expert tries to hack into your system. This a thorough and specialised service, which requires hundreds of (very expensive) resource hours. A pentest for a company only starting to address the security risks, this approach is like using a baseball bat to swat a fly — it will work, but is the cost worth it?
Security audit
A security audit, normally conducted by a financial audit company, measures a company’s security practices and governance structures in relation to a specific security standard. The auditor checks and verifies if the company is compliant with statutory regulations and the chosen security standard the company has implemented. For a company wanting to establish an information security function, it might not have the policies, procedures and other controls in place to justify a security audit. None of the options mentioned until now will provide the executive management team or IT operations with a good baseline understanding of their cyber risk with a road map on how to cost effectively start addressing key concerns.
An organisational security review will be able to identify the major information and cyber risks a company has, by incorporating a hybrid approach of vulnerability testing, reviewing the policies and procedures, evaluating the current cybersecurity readiness, and then to performing a gap analysis to determine the best, most cost-effective cybersecurity solutions available for the company.
CS-IT believes in the Pareto Principle, that 80% of your risk can be mitigated by addressing the top 20% of the causes. Cybersecurity solutions should be tailored to each company according to their own needs, risk appetite and budget. Should you like to know more about our cybersecurity reviews and roadmaps, please visit our website, or alternatively send me an email to [email protected].
- This promoted content may have been paid for by the party concerned

