 At TechCentral, we get called on average at least once a week — sometimes far more often — by a friendly sounding Indian national warning us that our Windows computer is infected with a virus. The call, which originates from a call centre, follows exactly the same script every time. Usually we shrug them off and put the phone down, but this week we thought we’d humour them to find out how they operate.
At TechCentral, we get called on average at least once a week — sometimes far more often — by a friendly sounding Indian national warning us that our Windows computer is infected with a virus. The call, which originates from a call centre, follows exactly the same script every time. Usually we shrug them off and put the phone down, but this week we thought we’d humour them to find out how they operate.
It should be noted that the consequences of their actions could lead to financial losses for you and you may even lose important documents on your computer. In short, never, ever, let these guys have access to your computer.
As this week’s call came in, the first thing the “operator” at the other end of the line tried to establish was who was owner of the Windows computer in the household. I’d taken the call. It was time to have some fun. I told the scammer that I was the PC owner. He proceeded to introduce himself as “John Connor”. I laughed quietly as I imagined Arnold Schwarzenegger’s Terminator hunting down this scamster in the streets of Calcutta. Perhaps he should have come up with a more convincing name.
“John” told me that my PC — along with my licence keys and personal information — was registered on their servers as being an infected device that was sending all my personal information out into the world.
He proceeded to tell me there were millions of users with the same problem and wanted me to believe his “company” was calling all of them to help disinfect their computers. He tried to sell his legitimacy by telling me that his company is a Microsoft affiliate called HelpnSecure.com. The website is clearly a front meant to make users feel more at ease.
This is where the scam starts getting clever, trying to fool the unsuspecting user that their computer is, in fact, infected with a virus. After I told “John” that I was sceptical, he proceeded to tell me that he would show me that my computer’s details were being broadcast to the world.
He asked me to jot down a number he said was my computer licence security ID, or CLSID. The number he gave me was 888DCA60-FC0A-11CF-8F0F-00C04FD7D062. To prove to me that he was telling the truth, “John” asked me to open my PC’s command prompt window. He used layman’s terms and guided me through every step. Little did he know that I know my way around computers.
Once I had opened the command prompt, he told me to enter “assoc”. This command is usually used to display or change file extensions and their associations. At the bottom of the list the command generated, the number he told me to jot down earlier magically appeared and I gave a fake gasp of surprise when he pointed this out to me.
The average computer user would never know that the CLSID number is not unique to their PC. In fact, every Windows PC will display this number as it is associated with a Windows function called “Send zipped file to target”. I told the scammer that I was very worried and he proceeded to the next part of his scam — showing me how many dreadful viruses had made their way into my computer.
To do this, “John” asked me to open my PC’s “Event Viewer” window, which is accessible by entering “eventvwr” at the command prompt. The Event Viewer in Windows displays every event that happens on the computer and the notifications are just that, notifications. Every Windows machine will show numerous warnings and errors in Event Viewer, but these are harmless and log everything from a USB drive that was pulled out too soon to an application that failed to launch for whatever reason. It does not show computer infections, but to a casual computer user — the real target of the Indian scammers — these events could look very worrying.
Once we had established that my computer was “fraught with infections” and that all my personal information was being broadcast to the world, “John” went in for the kill. He told me that engineers were on standby to assist me. This is where things got a little scary and it’s here where you should probably put the phone down if you’re also going to take these jokers for a ride.
“John” asked me to go to Support.me, a remote access service similar to Team Viewer — a service also used for this scam — that gives the crooks the ability to access your computer remotely. As I would be able to see everything that they were doing, “John” tried to reassure me that they would be able to solve the problem and that I shouldn’t worry.
We have a spare PC in the TechCentral office that has been newly installed and that contains no personal information. I used this machine for the next part of the ploy. I installed the Support.me application and provided “John” with the access details.
Once his “support engineer” was connected, “John” told me that there would be a service fee that I’d need to pay in order for them to help me. Prices ranged from R1 999/year to R3 500 for three years, he said, using South African currency.
The “engineer”, who now had access to the dummy computer, promptly proceeded to open PayPal in a Web browser. He then asked me to log into my account or pay via the credit card function on the PayPal website. Knowing that things were getting serious, I tried to stall him, but “John” realised I was not playing along.
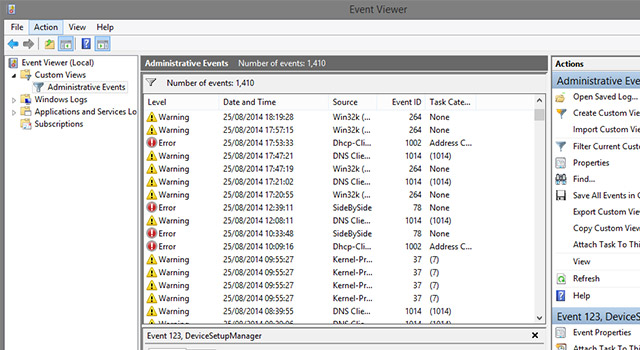
As they still had access to the computer, the next move proved a little puzzling. But I realised later what “John” and his “engineer” were trying to do.
Because I did not furnish my PayPal or credit card details, the scammers turned nasty and proceeded to my documents folder. I saw the engineer poking around in some folders, but I promptly disconnected the office Wi-Fi connection. After some research, I found out that they’ll delete system files and users’ personal documents.
Fortunately, I disconnected before they managed to delete files on the dummy PC — not that there was anything of value for them to delete.
If I had entered my credit card details or logged into my PayPal account, the scammers would have undoubtedly logged my details and stolen money as quickly as they could.
This scam can have serious repercussions, but considering the frequency of calls we get in the office, those behind it must have a reasonably high success rate.
So, if you get a call asking if you are the owner of the PC, just put the phone down. Or, if you’re tech savvy, why not have a little fun with them like I did? These crooks belong in prison, but there’s no harm in stringing them along provided you exercise due caution. In fact, it can prove quite entertaining if you have a bit of time to kill. — © 2014 NewsCentral Media

